
FusionPatch & FusionScan IT Services
How FusionPatch compares with other vendors
FusionPatch vs SCCM
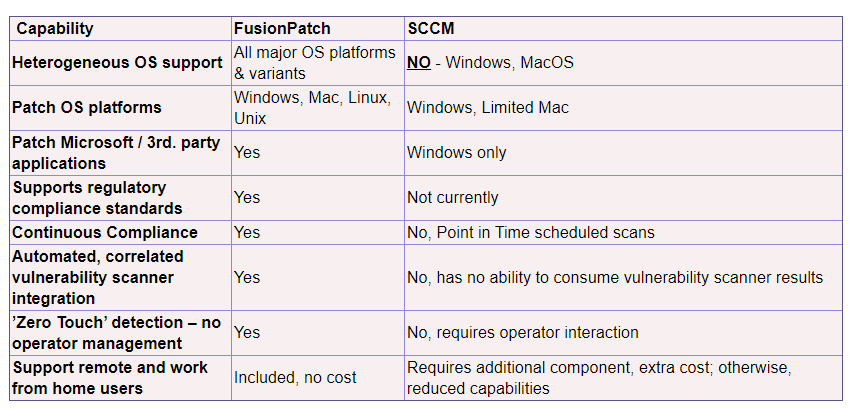
SCCM Cons
“Comes with a steep learning curve that has never been corrected, reporting is a big issue as you are writing SQL queries to gather information”
“We often need third party tools to make using SCCM acceptable”
“ It is very complex product which requires a lot of hands-on experience on both client and server operating systems with strong background in databases and reporting tools”
- SCCM Distribution Points are dependent on numerous underlying Operating System components to be working; otherwise, the Distribution Point will not function properly requiring considerable troubleshooting and maintenance placing additional load/stress on staff. Non-functioning Distribution Points can increase security risk since initial success rate is lower lengthening out the remediation process.
- SCCM agents can be fragile/brittle due to their dependence on Operating System components and MS Active Directory Domain membership. If either is not functioning properly SCCM can’t manage the system.
Why FusionPatch over SCCM?
Our Solution: FusionPatch doesn’t have these above dependencies/complexities making management straight forward with less stress on staff. This has additional benefits of reduced security risk due to extremely high 1st pass success rate while improving ROI/TCO.
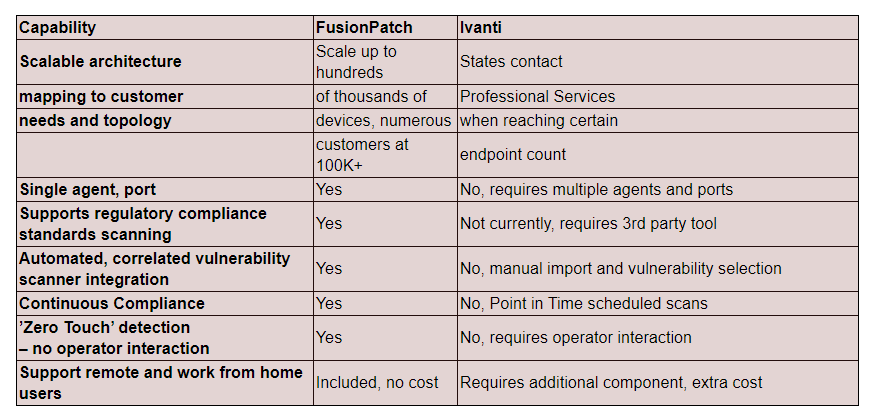
Ivanti Cons
- Ivanti is built upon acquiring disparate tools and attempting to integrate on the backend, which places considerable stress on staff to maintain (i.e. – care and feed) and troubleshoot the infrastructure.
- Additionally, Ivanti overall has multiple agents and port requirements that can add unnecessary load on the systems and risk due to the additional open ports.
- Another aspect is one of operator interaction/scheduling required to make sure the content is properly in place prior to taking action and scheduling the necessary agent configurations/settings for the point in time process. There is the potential for inadvertent operator errors leading in increased risk and lengthened out detection/remediation cycles.
Why FusionPatch over Ivanti?
Our Solution: FusionPatch doesn’t have these above complexities making management straight forward with less stress on staff. This has additional benefits of reduced security risk due to extremely high 1st pass success rate while improving ROI/TCO.
What can FusionPatch do?
- Single intelligent agent for continuous endpoint self-assessment and policy enforcement.
- Real-time visibility and control from a single management console.
- Management of hundreds of thousands of endpoints regardless of location, connection type, or status.
- Targeting of specific actions to an exact type of endpoint configuration or user type.
- Management of complexity and cost reduction, increasing accuracy, and boosting productivity
- Support for heterogeneous platforms.
- Automatic endpoint assessment and vulnerability remediation according to the National Institute of Standards and Technology (NIST) standards.
- Server Automation.
- Ensure continuous endpoint configuration compliance with effective remediation of configuration drifts.
- Supports security benchmarks published by CIS, DISA STIG, USGCB, and PCI DSS
- Collect, aggregate, and report on security configuration, patch and vulnerability compliance status of all endpoints against deployed policies.
- Report how vulnerabilities have been remediated to demonstrate compliance with regulatory or organization policies and pass audits more easily.
- Real-time enforcement of security policies across all endpoints, regardless of their network connection status
- Quarantine endpoints that are out of compliance and manage endpoint patching across operating systems and software applications to stay current and improve security posture.
Problem:
Difficult to keep up with vulnerabilities across multiple operating systems.
In addition, our company offers extenuation of our original CLM and PKI product offering for companies who would like to manage their Certificates Lifecycle process in combination with the PKI infrastructure and be able to have a centralized portal that allows customers to renew certificates in a single place vs jumping across different types of tools generating certificates and forgetting about them 3 years later only to result in outage.
- Many organizations are under the constant pressure to keep their systems and applications secure. Unfortunately, the task of keeping auditors happy and maintaining well defined balance between application usability and security is not exactly a walk in the park.
- Multiple operating systems have different types of vulnerabilities that can either be exploitable or not and rapidly changing.
- What makes it even more complex is the fact that Windows and Linux operating systems run different types of OS versions and not only OS versions, but happen to also host variety types of applications with different constantly changing versions, that happen to be hosting variety types of critical business processes that can under no circumstances be down.
- Anytime vulnerability is discovered, it opens up additional can of worms for internal IT staff, making their life stressful.
- Any vulnerability that is not addressed may result in rapidly elevated risk in the form of total system failure, ransom attacks or any other threats associated with critical resources.
- Many of the customers can’t keep up with the rapid nature of newly discovered devices (especially the type of devices that happen to have critical vulnerabilities) getting onto their network without being properly validated first, resulting often in rogue devices taking control of customers networks.
- Needless to say not having any type of formalized solution to address vulnerabilities is a major risk factor.
Challanges
Multiple Operating Systems Require Continuous Vulnerability Discovery.
Multi cloud and on-premise hybrid environments consisting of Linux and Windows devices require continuous vulnerability discovery, just like any other operating systems do.
Single Time Scans = Challenge
- Many vulnerability solutions providers on the market today provide vulnerability assessment services that solely focus around single time once a year or once every 6 month vulnerability assessment of critical servers, operating systems and applications, when in reality it needs to continuous process.
No Continuous Discovery for New Devices - Challenge
- Many of the security solution providers on the market today, have no concrete way of identifying if there are any new devices that got on their network, resulting gaps in security. (neither do they have any formal whitelisting processes to white list devices that are legit.)
Vulnerabilities often don’t get followed up on - Challenge
- Many vulnerabilities that do become discovered often never get followed up on, this is mostly due to the challenge of not being able to visualize the result of the patch updates in comparison to results of what the vulnerabilities looked like after patch updates were rolled out.
Needle in the Haystack - Challenge
- Many times when vulnerabilities are indeed discovered it’s hard to understand which vulnerability exactly is the most critical vulnerability.
Common Patch and Vulnerability Problems
How our FusionPatch and FusionScan can help customers reduce risk.
Problem
Difficult to keep up with patches across multiple operating systems.
Many organizations are under the constant pressure to keep their systems and applications secure. Unfortunately, the task of keeping auditors happy and maintaining well defined balance between application usability and security is not exactly a walk in the park.
Challenges
Multiple Operating Systems Require Continuous Patching
Multi cloud and on-premise hybrid environments consisting of Linux and Windows devices require continuous patch updates to keep systems secure.
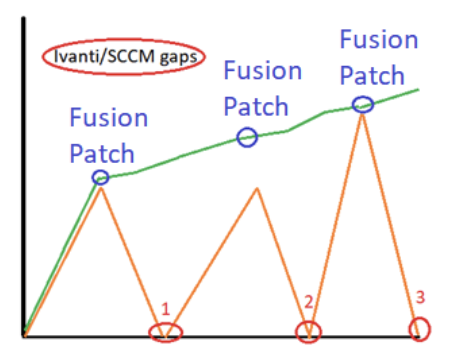
Point in time patching systems on the market today do not provide adequate level patching creating gaps & risks in the following ways.
For example, some of our competitor patching solutions on the market today such as SCCM or Ivanti relies on Point-in-Time level checking.
- Disconnected Endpoints – Off network, connection to Ivanti or SCCM servers
- Patch Tuesday – scheduled scan, produces critical visibility gaps.
- Reporting Gaps -only at scheduled check-in, produces visibility gaps
- Security – No visibility to changes except at check-in, increases risk.

Solution
FusionPatch Continuous Compliance checking
FusionPatch continuous compliance virtually eliminates visibility and compliance gaps associated with pre-historic and archaic point in time patching solutions that you see on the market today.
Solution
FusionScan Continuous Vulnerability Discovery Solution
FusionScan continuous vulnerability discovery solution makes the continuous process of discovering vulnerabilities based on CVE criticality score easy to follow. It’s a risk-based view of your IT, security and compliance posture so you can quickly identify, investigate and prioritize vulnerabilities.
- FusionScan Vulnerability scanning solution helps companies reduce security associated vulnerability risks, with pre-configured dynamic scans holistically configured to hunt for any new devices that get onto your network as well as existing devices, thereby helping customers take control of their network, visualize what vulnerabilities are present, which ones are critical and which vulnerability needs to be addressed first.
- Our FusionScan solution goes hand and hand with FusionPatch solution like brother and the sister solutions protecting it’s parent (meaning the company).
- FusionScan and FusionPatch uses different vendors,
What Can FusionScan Do?
With FusionScan customers can quickly
- Manage on-premises and powered by FusionScan most comprehensive vulnerability coverage with real-time continuous assessment of your network. It’s your complete end-to-end vulnerability management solution.
- Active scanning, agents, passive monitoring and CMDB integrations provide a complete and continuous view of all of your assets—both known and previously unknown.
- With coverage for more than 56,000 vulnerabilities, FusionScan has the industry’s most extensive CVE coverage and security configuration support to help you understand your security and compliance posture with confidence.
- FusionScan solution combines vulnerability data, threat intelligence and data science to give you an easy-to-understand risk score so you know which vulnerabilities to fix first.
- Centralized network management to facilitate reporting and management of multiple consoles, scanners and assets.
Support Model
Both of our solutions FusionPatch and FusionScan are delivered with 24 by 7 support.
Next Steps
Q/A
Let us know a little more about your environment.
Is the solution needed for on-premise or in cloud resources or combination of both?
Is the need only for Linux and Windows servers for now?
Design Document and Cost
If interested moving forward with the solution we can provide separate presentation for that, covering high level technical solution overview and costs. To learn more contact us either by the phone number on the top right corner, or filling out the form by clicking Get a Quote button. Or send us a chat message on the bottom right corner icon.
Want to go beyond FusionPatch and FusionScan to further reinforce security in your environment?
Multi Factor Identity Validation Services for small, medium and large size businesses
If so don’t hesitate checking relevant cyber security monitoring and integration services below. We work with multi vendor environments, helping customers not only with patching Linux and Windows workstations, but also provide comprehensive multi factor validation services for other devices ranging from video conferencing systems, printers, Cisco or Avaya IP Phones, mobile Android and IOS phones, Macintosh laptops, Virtual servers running on ESX hosts and many others. If interested to learn more for how we can help customers validate if their device is truly their company’s device, then don’t hesitate to check out our Multi Factor Identity as a Service solution.
Want to be a bit more pro-active with your vulnerabilities?
Vulnerability Threat Hunting Services with Sumo Logic
- FusionPatch and FusionScan solutions do offer visibility of vulnerabilities solution, but many customers want to actually react to vulnerabilities discovered beyond simple recommendations and actually want to see whether or not they are actively being exploited and want to see some sort of indication that they are being targeted.
- Our company can help customers identify vulnerability threats that may very well already exist in your environment, yet require some type of logic to be identified and remediated. Some of that logic is as simple as turning on additional debug logs within your appliances or application and then feeding the output of these logs into dedicated SIEM such as Sumo Logic, Splunk or others.
- Our company specializes in crafting specific queries that are based on your very own existing vulnerability vendor recommendations, helping customers grasp the concepts of reality and criticality of the vulnerabilities present within their network. Not only do we help customers identify what the threats are based on the existing vulnerabilities, we additionally work with customers to help them build common threat identifiers based on MITRE ATT&CK knowledgebase, helping companies focus on critical indicators, threats and risks first… before focusing on anything else.
- This is slightly different than the offering from FusionPatch and FusionScan since this service is focused on creating customized dashboards per specific customer needs, helping companies reinforce their security.
- If interested in this service then don’t hesitate to check out Vulnerability Threat Hunting with Sumo Logic Service.
Want to minimize certificate related outages?
CLM and PKI Management Solutions at your Service
- FusionPatch and FusionScan offers solid foundation for your patching and vulnerability discovery needs, but they don’t exactly include certificate life cycle management and PKI infrastructure management services.
- If you have been placed in charge of your security posture and seeking a way to minimize major incidents, then taking control of your PKI and Certificate life cycle management process is probably a good idea. To see how our company can help you keep track of certificate life cycle and centralize certificate deployment across multiple types of devices with specifically crafted solution for your organization, click this link CLM and PKI Cyber Security Management solutions.
Want to monitor your applications and networks beyond vulnerabilities?
Although FusionPatch and FusionScan is a set of great foundational security solutions for company’s organization, in reality many of our customers want more. Specifically many of our customers want to monitor their infrastructure and applications in cloud and on premise.
Our specialized subject matter monitoring experts can help companies take control of their organization and bring additional visibility into critical applications and infrastructure running either across monolithic applications or containerized microservices architecture. Our company specializes in different monitoring vendors, ranging from SumoLogic, New Relic, Logic Monitor, DataDog, Splunk, Zenoss, AppDynamics and many other monitoring and SIEM systems.
To learn more about our monitoring offerings visit any of the links below
- Sumo Logic Monitoring Assessment for Financial Industries
- Logic Monitor Integration Solutions and Services
- Solar Winds Consulting
Industries We Service and help customers integrate patching and vulnerability solutions.
Travel and Aviation
Consulting
We help companies monitor Airport Networks and ATM devices, as well as wireless access points.
Financial Services
Consulting
Our company helps Loan Processing firms, Banks, and other financial institutions monitor combination of both on premise and in cloud resources.
Education
With Entuity we can monitor Campus networks for real time changes on infrastructure such as firewalls, routers, switches, SDN controllers.
Law Firms
We also work close with Law Firms and other types of legal organizations seeking to monitor their cloud and on premise resources.
Manufacturing
Our company can help customers add foam spray pumps, or any other types of manufacturing devices, or IoT devices into Entuity monitoring software.
Accounting and CPA firms
Our company helps CPA accounting firms monitor their network for newly discovered devices, and changes in data.
With FusionPatch and FusionScan we can help protect the following devices.
We can scan for printer vulnerabilities and assist with printer patching.
We can scan for vulnerabilities in Video Conferencing Systems and assist with Patching Cisco Webex based units, Polycom or other.
We can patch phones that are vulnerable with latest software images through CUCM, while ensuring that they are also 802.1x compatible. Plus with FusionScan we can scan network to see what phones are vulnerable.
With FusionScan we can scan company’s network to see what devices are vulnerable and with FusionPatch we can patch vulnerable laptops helping customers minimize risk.
With FusionScan we can scan for vulnerabilities within your existing environment across physical or in cloud servers or other infrastructure and see which systems are vulnerabile. Then with FusionPatch we can assist with patching vulnerable systems.
Patching and Vulnerability Problems & FusionPatch and FusionScan solutions
With FusionScan we can help companies scan for new vulnerabilities based on schedule or on demand and see if any new vulnerabilities are shown on your network.
In addition to visualizing your vulnerabilities we can keep track of which ones have available exploit.
Our company can help onboard many different types of devices on premise or in cloud with certificates and integrate them with 802.1x Cisco ISE, helping customers take control of their network.
We can integrate FusionPatch with other monitoring tools such as your existing SIEM or Sumo Logic tool visualizing what vulnerabilities were resolved and on what systems.
Although with FusionPatch or FusionScan we can’t exactly tell if one of your devices are actively being exploited, nevertheless FusionScan will still indicate if there are any vulnerabilities with Exploit available on the internet that have been found on your network.
However, we do offer separate service where we actively conducting threat hunting monitoring on any devices that were exposed to vulnerabilities with active exploit.
Other Integration and IT Services Similar to Patching and Vulnerability Management
-
AlphaCICE & Alpha FusionView Service Details
Read moreMinimize false positive, duplicate alerts with AlphaCICE central intelligence correlation engine. AlphaCICE and unify all of your tools AIOPS events in a single pane of glass with Alpha FusionView. See how Alpha FusionSmart Enterprise Monitoring service that Alpha Technologies offer ties it all up together in context of multiple ITIL best practices phases.
-
AlphaCICE – Central Intelligence Correlation Engine
Read moreMinimize false positive, duplicate alerts with AlphaCICE central intelligence correlation engine. AlphaCICE is a custom solution and service offered by Alpha Technologies that is specifically designed for financial industries seeking to take control of their incident management process. Incident Managers can maximize their operational effectiveness through streamlined operationalized workflows, by relying on correlated supervised and unsupervised AIOPS classified intelligence fetched from your already existing monitoring tools. AlphaCICE is explicitly designed to reduce multiple events into a single actionable event that matters most, by empowering data owner operators with prescriptive & AI & ML driven recommendations
-

Alpha Digital Transformation of Applications & Tech Stack
Read moreAlpha Digital Transformation solutions for all size businesses seeking to secure their legacy application in order to minimize risk, while in parallel migrate the application and tech stack into modern API invokable and event driven ecosystem helping data owners get closer to their data.
-

Alpha AWS | AVD | Office 365 Virtualization Solutions
Read moreAWS Desktop and Network Virtualization solutions and services for small, medium & large size companies seeking to solve high latency connectivity related problems, while maximizing security.
-

Alpha FusionChain Innovative Solution for BlockChain Database and Monitoring
Read moreMigrate Your Legacy applications to Blockchain faster and safer without disruption of the existing workflow. With our tool kit we can help companies build, deploy maintain and manage Blockchain architecture helping you revolutionize your microservices and decentralized architecture. We can build Blockchain networks for multiple use cases ranging from NFTs, Crypto, MetaVerse and beyond.
Why Customers Pick Us

Automation of Applications
Automation of monolithic and microservice types of applications, software testing and quality assurance. Helping companies minimize manual tasks in every day operations and reduce costs by leveraging custom built automation scripts for your enterprise infrastructure, ranging from automation of APIs to orchestration of complex resources.
Read More
Expertise in Cloud and On Premise Environments
Expertise in AI and ML with multiple clouds AWS, Azure, GCP, Kubernetes, Serverless Lambda Functions, Docker containers, and beyond as well as on-premise network & app infrastructure environments.
Read More
Unified View
Custom-built view bridging your micro-services and monolithic application, infrastructure, and monitoring need all in one portal. For example, ServiceNow, Jira, CMDB, BMC Control M and Microservices all in 1 portal, helping customers visualize, slice, and dissect data as well as create reports, trends, and forecasts, based on results of any data, either coming from your on-premise or in cloud environment
Read More
Based on Zero Trust Connectivity Architecture
Get your on site locations and remote office work force or IoT devices connected with the help of custom solutions designed to keep companies secure, while protecting employees form malicious threats.
Read More
Certificate Authority Validation & Renewal
Certificate Lifecycle Management (CLM) and PKI services and solutions for companies seeking to take control of their certificate validation and enrollment needs, helping companies reduce risk through auto renewal.
Read More