
Our company offers, digital transformation and security solutions and services for small/medium and large size businesses seeking to secure their vulnerable applications while simultaneously transform them.
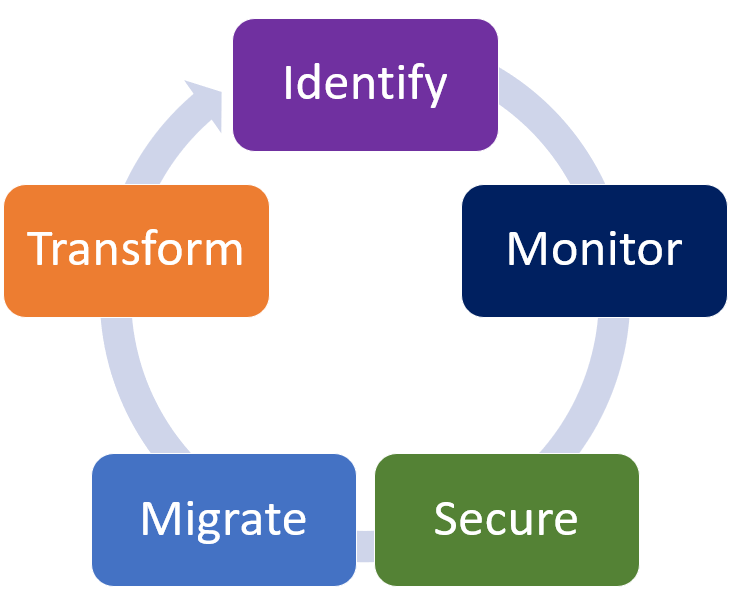
Our company DBA Binary Fusion, Subsidiary of Alpha Technologies. can help your legacy application that maybe already vulnerable become secured using DMZs or Zero Trust Access techniques as a temporarily work around, while in parallel help you migrate your existing application and it’s underlining tech stack into more modern, event driven, API friendly, serverless or containerized architecture.
- Helping you address immediate compliance risks while simultaneously paving the road map to tech enablement exploration of data, and optimal latest and the greatest application experience.
- Helping your users get closer to the data using the language of their choice.
- Improving batch processing speeds.
- Migrating out of traditional architecture into serverless more modern event driven, serverless environment.
All that while creating secure demilitarized channel between users who are suppose to be accessing legacy application, while migrating and transforming legacy application into microservices takes place in parallel.
Why use DMZs or Zero Trust Access Methods to secure legacy applications ?
It’s no secret that if compliance and risk is asking you to take control of vulnerability. There is not that many options, other than to either shut down the existing application or solve the vulnerability, by upgrading vulnerable application.
- Attempting to upgrade legacy application that is homebrewed with custom code that was developed in house, is not exactly walk in the park.
- Turning it off application that is still possibly being used in order to resolve vulnerability is also not a great option.
- Having other applications and devices to worry about in the process of maximizing security doesn’t exactly help with sensitive risk and compliance requirements either.
- Trying to decipher whether or not vulnerability is being exploited and indeed your users are impacted is not exactly trivial either.
In situations like this it’s best to address the problem the best way you can, without introducing large risk and instead utilizing Quick Win Approach to secure and demilitarize vulnerable application/device, while still providing access only to users/devices that absolutely need access.
How to secure vulnerable application while being under the gun of risk and compliance
Securing application that is homebrewed, monolithic in nature, and tightly interlaced with business logic requires quick win demilitarized approach.
Isolating vulnerable monolithic application into DMZ or what so called sandbox environment, where only specific set of users and devices are allowed access into while blocking everything else.
- Doing so requires massive amount of understanding about the application itself and underlining critical processes that are running, dependencies, inbound user/devices connectivity and many other details that not every company is willing to undertake before pulling the plug.
Here is couple of reasons why that is the case.
- Heterogenous systems.
- Tightly coupled dependencies.
- Minimum documentation.
- Almost non existent visualization and monitoring.
- No Infrastructure as a code flexibility.
- No existing east to west traffic controls.
- Minimum north to south traffic visualization.
- No authentication NAC systems.
- No 802.1x Controls
- No ingress firewalls.
- Complex on premise or in cloud environment.
- No Security VPC
The list above is only small part of the challenge
What you just seen is a small fraction of the reasons why securing legacy-based applications is highly challenging. What you just seen applies to the nature of the application itself and overall environment.
- Securing application into DMZs is the way to go. How you go about it whether it’s through Zero Trust Access methods or traditional methods, ultimately depends on your existing architecture and capability of your existing architecture.
- If your security infrastructure and architecture does not have adequate level of controls, the not only does your entire app needs to be transformed and it’s underlining tech stack, but the security infrastructure also needs to be modernized and digitally transformed.
Let's say you do isolate legacy application as a temporary workaround what's next?
Even if you do temporarily isolate application using demilitarized quick win approach, and ultimately minimizing user and device access to vulnerable legacy application while providing access to few users who still need access in order to reduce risk foot print, you still would be left with some left over challenges.
- For example your users who are still accessing vulnerable app, need to be accessing it in a way that they themselves don’t get infected.
- That requires invoking special threat hunting techniques on these sets of users who are still accessing vulnerable application, as well providing virtualized sandbox jump box environments to such set of users.
- Some of these actions can be done sequentially over time, dependent on criticality.
Let’s say users who are still accessing vulnerable home brewed application, got infected, and start spreading laterally malicious virus infection. That wouldn’t be fun…
- Having high degree of visualization on such users or isolation of users into their own set of DMZs is also highly advisable.
- The problem starts with the fact that remote users who are accessing such applications are not exactly governed by the same rules and policies as users who are working from office.
- The result of such inconsistency can bring additional risk factors.
That is not to say that you shouldn’t be doing any of these quick win demilitarized approaches, but rather to say that there is entire ecosystem of complexities with this endeavor.
So what shouldd the company do?
In such case, company should have concrete road map for solving not only legacy application problem, but also solving underlining security architecture problem along with solving the underlining tech stack problem, while simultaneously executing these demilitarized quick win approaches in order to reduce risk.
- All that while setting up threat hunting and managing higher degree of scrutiny on source devices and source users attempting to initiate connection with vulnerable system.
- All that while setting up monitoring and testing techniques, alerts and exploitability finding procedures.
- Not exactly walk in the park, but luckily DBA Binary Fusion, Alpha Technologies can help.
How exactly can we can help?
Whether you have firewalls in your environment or simply routers, or any other type of infrastructure.
- Our company DBA Binary Fusion, subsidary of Alpha Technologies can help you navigate complexities around your homebrewed application.
- Creating demilitarized zones, and isolation controls to contain your vulnerability in house, without letting it become exploitable.
- We have created unique DMZ Quick Win security approaches that leverage different types of technologies to provide temporary methods of security, until your application becomes migrated.
- We can either help you isolate your application, by first setting up monitoring controls around it, and analyzing business logic.
- We have our own monitoring software and techniques to track traffic flow.
The best part about it we are flexible, we can either work on your existing architecture or augment your existing company with additional set of DMZ Engineers, who can help with securing your legacy and non legacy applications.
We can help in parallel to securing your legacy application, transform both your underlining tech stack and security/networking architecture.
- We have created unique approach in analyzing customer’s networks whether it’s office or remote or mobile.
- Our infrastructure security transformation approach is scalable across multiple clouds, different vendors.
- We work with different vendors, helping you save money on the existing vendor engagements that you may already have.
In combination with transforming your on premise and cloud architecture, we also help companies transform their middle tier and back end infrastructure that vulnerable application is relying on.
That means making infrastructure multi cloud driven, API friendly, event streaming, and modern.
In addition to executing quick win demilitarized approach, we help customers transform their existing DMZ architecture into Zero Trust Access architecture.
- Helping companies migrate out of VPNs into Zero Trust Access solutions, helping companies standardize their wired and wireless policies across single central software defined networking controller based architecture.
- Making it possible for companies to have consistent policies across both remote and in office environments, while providing high degree of visibility and security capabilities across multiple users and devices..
- We work with multiple Zero Trust Access vendors to help your traditional networking environment become transformed into something greater than what it is now.
- Making it possible to create user and group eccentric policies to limit access into vulnerable applications.
Our job wouldn’t be done without helping your company migrate to latest and the greatest application framework such as REACT, making it possible for your users to experience application performance faster and easier in a more friendly API driven way.
- We can help you transform your application from monolithic architecture into microservices and serverless architecture.
- The best part about it we can do this in parallel to securing your legacy application, while paving the road for success, and maximizing performance, security and data exploration capability for your users.
- All that while extenuating functions of your legacy application into more modern and snappier interface. Improving UI/UX and automation capability.
Over the years we have created frameworks for how to transform monolithic applications into microservices, and have done this level of transformation for many other large size companies.
We can work together with your existing team, by either helping you transform your application, while you existing team secures it, or do combination of both.
Additionally we can help your company construct a road map for digital transformation helping you introduce tech enablement into your organization, event driven activities, and bridging machine learning, data analytics and business process management systems together into single unified application.
Other types of services we can help you with
We know that securing applications is not exactly walk in the park, especially when it comes to isolating them. As part of our isolation techniques we use Desktop and Virtualization techniques.
Further down below you will see some of the challenges with these virtualization technologies and how we can help you navigate around such challenges.
Challenging Types of AWS environments that we can help you navigate
AWS Environments with existing VPCs
- If you already have your environment setup, and happen to have bunch of EC2 instances hosting all sorts of applications, but not sure what changes to make and how to make them while providing capability for users to connect remotely, then worry no more, with our help we can evaluate your existing environment and provide concrete recommendations for what to change, when to change it, and how to do it with minimum impact.
- Our goal is to help your employees and consultants, get together in order to improve productivity, connectivity and security of your environment.
On premise to AWS using AWS Workspaces
Our company offers the following services.
- Creation of Virtual Private Gateways in AWS cloud.
- Creation of ACM certificates.
- Creation of Simple AD, or integrating with your existing AD.
- Maintaining and building your AWS Workspace images.
- Distributing AWS Workspace clients to the users.
- Monitoring AWS Workspace usage.
- Modifying Security Groups to allow access.
- Assisting your employees with AWS Workspace installation, troubleshooting.
- Level 2 Support
- Level 3 Support Engineering and Architecting your environment.
- Integrating your environment with your existing networks, DNS, Proxies, Load Balancers, Kubernetes clusters.
- Testing your environment and a lot more.
Professional IT Consulting
For Small Large & Medium Size Businesses
Desktop Virtualization Solutions.
Virtualization Troubleshooting
Here is what we help customers with when it comes to making any of these virtualization solutions or VPN tunneling technique work for your environment.
When Troubleshooting AWS Workspaces
- We Verify if users have TCP and UDP connectivity.
- We verify entire Layer 1 through Layer 7 connectivity.
- We obtain Elastic IP Addresses and ensure that these IP addresses are allowed proper access.
- We debugging connectivity issues with ISP in the event session drops.
- We run Traceroutes, gather packet captures.
- We test out applications when logged into Workspaces.
- We troubleshoot MFA related issues.
What was just described is a partial list,
AWS Desktop Virtualization Management Servcies
Here are the services that we offer from AWS perspective.
- Design of your entire Virtual Architecture.
- Creation of EC2 instances with correct software installed.
- Creation of auto scaling groups, creation of AWS Workspaces architecture and integrations between AWS Workspaces and your existing EC2 servers.
- Creation of VPCs and associated EC2 instances with appropriate AMIs to run your vendors firewalls in the cloud. (this is for cloud to cloud security)
- Creation of site to site VPN connections, leveraging either routed based VPN approach or policy based VPN approach. (this is for interconnecting your other offices)
- Configuration and management of your AWS routing. (this is so everything is managed centrally and every node can get to the other node)
- Security group management. (this is to ensure security)
- Permission management. (this is to ensure that only right people get access to environment)
- Cloudwatch configuration for metrics and logs. (this is to visualize your AWS environment health status)
- Transit Gateway VPN configuration. (this is to reduce mesh peering between VPCs and centralized the connectivity across transit gateways)
- Virtual Private Gateway setup for small and medium offices. (this is a cloud native AWS VPN option to connect to other on premise sites or offices)
- Certificate ACM building, helping you create certificate authority and making certificate based authentication work. (this is so your security up to date, and your users don’t get warning with certs)
Cost Analysis & Savings
When many of our customers reach out to us, rarely does every customer know all the associated costs with the solution, simply because there are many factors associated with creating Desktop Virtualization solutions and building VPN tunnels and making them work with the cloud.
As part of our solution offering, we help customers pick the most optimal cost-effective options for their connectivity needs, and part of the engagement conduct Network Assessment, making sure that whatever existing infrastructure that you already invested is factored into the solution, helping customers save money.
AWS Cost Analysis for having site to site VPN or any type of VPN solution
As part of the solution, we help customers analyze licensing costs for AWS Workspaces or Azure AVD or Office 365 or Virtual Private Gateways or Transit Gateways in AWS helping customers make informative decisions about the cost factor prior to engaging with the solution.
We also help with AWS licensing cost analysis for ACM certificate management solutions for any EC instances that you may have that require careful tracking.
- For every location we recommend customers to use multiple types of solutions and VPN tunnels for redundancy, each tunnel has a cost factor associated with it.
- In fact we tell many customers to use multi cloud based redundancy setups, simply because we seen entire cloud going down.
- For example to some customers we recommend using AWS Workspaces, while in parallel for resiliency recommend customers setup docker containerized VPN tunnels across Kubernetes/DockerSwarm clusters, using something like Strongswan.
- For others we recommend something as simple as OpenVPN solution or WireGuard to connect from on premise to cloud instances.
Docker Virtualized VPN Gateway Instances
Docker Virtualized VPN Gateway Instances
Additionally, we help customers get connected using docker instances. Some of our customers have compliance requirements where every tunnel must be separated in a form of a distinct channel. Where multiple sites or IoT need to connect to a multi cloud network, spanning across different clouds.
- To do that we recommend customers virtualize tunnels within dedicated docker instances and run these tunnels across Kubernetes clusters or other types of clusters spanning across different clouds.
- Doing this approach makes VPN solution scalable, and at the same time distinct. This approach does have advantage of relying on distinct multi cloud based architecture, not dependent to the principles of single cloud provider.
- Using for example combination of multi docker based approach plus AWS Workspaces can provided companies high level of resilience, using distinct types of architectures, minimizing business disruption possibility.
With Dockerized Virtualized approach you are not exactly virtualizing the Desktops, but rather virtualizing the VPN channels, where each channel provides access to applications directly on your cloud networks.
The Dockerized use case can be very good one to execute for IoT tin the field type of applications, that require secured connectivity to cloud.
Docker VPN virtualization using Infrastructure as a Code
With Docker based VPN Infrastructure as a code comes to play
Whether you are a start up or a medium size companies or a large size company, you may have heard of Infrastructure as a code concept.
Setting up docker containers with VPNs running inside of them across different clouds and executing changes in each of these tunnels, maybe difficult thing to do without relying on some type of CI/CD pipeline.
- Our company can help you scale your existing connectivity whether it’s from on site offices or from mobile devices, or from IoT devices in the field.
- We have created CI/CD pipelines in the past that can help us orchestrate complex VPN tunneling connectivity needs across multiple geographic regions running across multiple cellular networks, helping customers maintain connectivity to their IoT devices or offices.
Bringing together multiple in office or remote users, Endpoints, or IoT devices in order to satisfy your company’s business case is precisely what we can help you with.
Desktop Virtualization technique is only one part of the puzzle. Many of our customers have many different integration needs and puzzles to solve, including network & desktop virtualization needs.
- Imagine bridging desktop virtualization technology with other facets of your business connectivity needs in order to improve security, connectivity and visibility.
- Imagine running less risky network.
- Imagine having less headaches with integration puzzles.
You do not need to imagine anymore, contact us to help you with your use case. Helping you take your connectivity needs under control, while minimizing costs.
Licensing cost Analysis
When purchasing any type of desktop virtualized solutions, equipment or software relevant to firewalls, or VPN termination devices there are always licensing fees.
We can help you analyze these licensing fees and pick the right partner for your connectivity needs.
We are vendor agnostic
It doesn’t matter with which vendor you are dealing with, we are vendor agnostic.
- Some vendors may be better than others when it comes to individual solution needs.
- Our role is to recommend the best vendor to help you save money
- Regardless if you are looking for firewall in the cloud solution, Desktop Virtualization or Zero Trust type of solution, we can help you integrate it.
Our Alpha Technologies team don’t speak the vendor language, but rather speak the protocol language.
Think of it this way, every vendor who builds some type of solution is relying on some type of protocol to make the solution work.
Our company has specialized IT Network & Security Consultants who are well versed with both on-premise and cloud types of Network and Desktop architectures, regardless if it’s AWS, Azure, Google.
Why Transform your applications while simultaneously securing them?
Problem
Migrating Legacy App is like solving a murder mystery.
Many organizations have vulnerable legacy apps that must be resolved in order to minimize risk, attempting to migrate out of legacy app to new architecture is like trying to solve a murder mystery.
For the following Reasons:
Vulnerabilities Deciphering can be difficult
Companies constantly scan their applications and devices for vulnerabilities.
In many cases some security vulnerabilities can be resolved and in other cases, there is absolutely nothing that can be done since application requires major reverse engineering and running on legacy code and tech stack.
Securing application not trivial
Attempting to secure legacy applications is also not exactly easy thing to do. Knowing what type of vulnerability is and how it behaves is not exactly trivial, especially if company has a lot of legacy applications.
Application can infect others
Imagine what if this legacy application that was just discovered to be vulnerable starts leaking out through east and west, north and south directions infecting other applications, that would be pretty bad right?
Application is residing on legacy Tech Stack
- Application running on old monolithic processes, difficult to decipher.
- Application is relying on legacy batch driven backend architecture vs event streaming.
- In some cases reliant on legacy data warehouses and data marts.
- Not cloud and API consumable. Running on legacy traditional SQL databases for back end.
- The front end of application running on legacy Angular code vs REACT.
- No slicing and dicing functionality or other advanced functionality present.
- Application running on iFrame or other legacy frameworks.

Solution
Secure existing app and transform in parallel - find out how here.
Secure Existing App First
As you seen earlier the problem that many companies face with traditional applications is that the vulnerabilities run ramped in many use case where code and framework that the applications are running on is not migrated to the latest and greatest.
How to Secure it?
However, that does not mean that you can’t intelligently secure application at least temporarily with access restricted to only certain users from jump boxes where threat hunting is enabled, minimizing the infection perimeter and still allowing your existing users to work who absolutely still need to work using this legacy type of application.
Threat hunting setup and increasing your vigilance on high risky app is the key in making sure that that only small subset of users can continue to use application.
Alpha Technologies can help you secure your application temporarily, just so you can contain the risk to the minimum, while simultaneously help your legacy application undergo digital transformation journey.
That Journey would involve, conducting discovery and assessment, monitoring for existing software behavior prior to transforming it.
Then migrating your application and underlining tech stack onto modern Event Driven microservices/serverless architecture, as well as making it API consumable and accessible, while introducing additional enhancement features that can maximize your employee’s productivity while accessing applications faster.
Alpha Technologies has engineered the framework and created unique approach for helping companies in parallel secure and transform their application and architecture.
In this Digital Transformation solution and services article we will describe how exactly can we do this.
Typical Example of what our customers ask us to do
Quickbooks remote users need to connect to open up Quickbooks app
We get some customers who reach out to us and ask us to figure out how to connect their CIFS/SMB applications such as Quickbooks to their remote employees.
- Problems that we instantly see with customers is the fact that solutions that rely on VPN do not exactly work with the Quickbooks.
- To solve this problem, we advised the customer to bring the data closer to their Quickbooks Server.
- In this case we explored several solutions initially we tried Sophos Firewalls with site to site IPSEC VPN tunnels from office where users were residing to AWS using routed VPN tunnels.
- That approach worked for some applications, but only was relevant for in office users and not exactly for out of office users, and this approach wasn’t working with Quickbooks.
- In simple words, users were able to open up file shares, but Quickbooks was too sensitive to limitations of CIFS protocol being too chatty, as a result of that chattiness, Quickbooks file simply couldn’t be opened.
- Traditional IPSEC VPN tunnels didn’t do the trick.
- Then we tried OpenVPN which basically uses port 443, slightly similar concept, and although this helped remote users to connect to all sorts of other applications that customers had in AWS cloud, Quickbooks application still had the issue.
- At this point we knew that unless we make Quickbooks client reside on the same network as Quickbooks server, our chances of success would be slim to none.
- Customer was happy with his OpenVPN solution since it did provide alternative method of architecture for his remote work from home users and in office users as oppose to using Sophos, but not happy about not being able to open up Quickbooks.
- Explaining limitations of CIFS protocol to typical customer, is not exactly easy thing to do. In customer’s mind they think application should be able to open regardless where it sits.
- Several approaches were researched to address customers problem, these approaches included AWS RD Gateway and AWS Workspaces.
- Upon trying to use AWS Workspace to connect to existing EC 2 Quickbooks server instance, surprise, surprise, even with AWS workspaces access to the Quickbooks server wasn’t possible to achieve.
- We did end up using other type of solution with RD Gateway to achieve it, with specialized load balancers and auto scaling groups.
- We also helped customer integrate Simple AD with his users.
Whatever the case is for every problem there is a unique solution.
Whatever the case is for every problem there is a unique solution.
- In the case of this situation perhaps easier solution could have been to add Quickbooks Server on the same subnet as Workspace client…. but customer wasn’t willing to do that… and preferred another approach instead.
- At the end of the day, customer was happy with all approaches that we iterated through.
- This type of engagement just shows you how many different POCs and iterations we go through.
- For something that we have done before we can gladly do POC for your company, before engaging into actual solution to help you gain degree of confidence.
- However, if it’s something new completely new and application is home brewed or highly sophisticated and running on incompatible with network protocol such as SMB/CIFS, that POC will not exactly be free of charge.
- For the simple reason of complexity and different variables as what you just seen in this use case.
If you have an existing start up company or small company or medium size company and seeking to construct some type of solution to help your business connect. Then don’t hesitate to reach out to us for your assessment, customized presentation, demo and POC free of charge prior to engaging with us.If POC is outside of our comfort zone, then there will be fee associated with that, depending on the level of complexity and research that would need to do.
Additional Services for Identity Validation and Network Monitoring
In addition to offering Desktop-Network and Application Virtualization services our company also offers multi factor level of validation across either certificates or other validation characteristics helping your networks stay secure.
We also can help companies visualize their entire environment in tools like New Relic,DataDog, LogicMonitor, SumoLogic, AppDynamics, Zenoss or Splunk, Solar Winds.
For more info visit our monitoring services.
- Connecting through VPN is one thing, but ensuring that the person who connects to your VPN is legit company’s employee is another.
- Imagine being able to visualize your configuration changes on switches, routers or firewalls, as well as changes within your infrastructure environment ranging from actual physical infrastructure as well as cloud, whether it’s Kubernetes clusters or Serverless Microservices.
- Imagine being able to visualize business transactions as it pertains to generic health score of your entire application or business service, or being able to visualize unique business processes not just from metric standpoint, but from logs.
- Imagine being able to visualize distributed tracing patterns as users navigate through different types of business transactions and how overall health of your application depends on the infrastructure components, application components and other dependencies.
- Imagine being able to visualize even complex recurring events that need to be factored into alerting, but require intelligent logic adjustment.
- Imagine being able to suppress alerts and tackle seasonal type of data, in order to minimize risk of not being alerted when you needed vs when alert is not really needed.
- Imagine being able to have predictive and forecasting monitoring that can combine previous cyclical data in combination with other factors that are relevant for your environment and be able to get alerted on that.
- Imaging having different types of dashboards for compliance, operational level and many other levels, in combination with repots being sent to you or other team members helping your team minimize risk and look like a super hero.
Imagine being able to see when failover happened, at what time, when the VPN tunnel failed, and be able to see it all in the same screen with the business services that were impacted around the timeframe when connectivity was down.
Imagine being able to visualize your Virtual Private Gateways their connectivity status, what tunnel is up, what tunnel is down, as well as other statistics, from your on premise firewall and be able to see health of your environment.
Well with so many imaginative points... described above, you do not have to imagine anymore.
Simply reach out to our DBA Binary Fusion company tell us your use case and we’ll hit the ground running supplementing your existing IT Staff with super charged monitoring and cyber security expertise, that can help your organization reduce risk and best of all tackle complicated tasks that otherwise would not be possible to tackle without a strong IT Security and Network/Application monitoring expertise.
When contacting us, simply let us know the use case you are working on, what you are trying to integrate, what you need monitored, how you are trying to integrate, what tools you already invested and need help with. Or simply describe the challenge you are facing. Our company is very agile and flexible in the way we conduct business. If interested in our services feel free to reach out to us, so we can share with you some of our service offering demonstrations and see if we can do POC or POV for you.
We work with financial organizations as our core expertise, but also service other types of industries ranging from real-estate, manufacturing, professional LLCs, accounting firms, health/medical dental, entertainment industries and other types of industries.
In Summary
- Desktop Virtualization configuration can be very challenging and almost impossible to configure without advanced knowledge in security and networking protocols.
- Our company makes the complexity fade away.
- Picking DBA Binary Fusion subsidary of Alpha Technologies as your company’s IT resource for advanced type of networking integration will help you save tons of time, doing it yourself.
- Reach out to us, let us know your use case, we can get together analyze what you have, and provide your recommendation on how to move forward with what tool, what to monitor, how to monitor it and can also provide you presentation for some of the services that we did for our other customers in the field of Machine Learning, Certificate LifeCycle Management, Network Monitoring and beyond.
- If interested send an email to [email protected] and simply let us know your name, company name, phone number, and what you are looking for, or alternatively contact us by the phone number shown on the top right corner of this website.
- Thank You for taking your time to read about our Logic Monitoring Services and Solution Integration services.
Industries We Service and help customers integrate Multi Factor Solutions
Travel and Aviation
Consulting
We help companies monitor Airport Networks and ATM devices, as well as wireless access points.
Financial Services
Consulting
Our company helps Loan Processing firms, Banks, and other financial institutions monitor combination of both on premise and in cloud resources.
Education
With Entuity we can monitor Campus networks for real time changes on infrastructure such as firewalls, routers, switches, SDN controllers.
Law Firms
We also work close with Law Firms and other types of legal organizations seeking to monitor their cloud and on premise resources.
Manufacturing
Our company can help customers add foam spray pumps, or any other types of manufacturing devices, or IoT devices into Entuity monitoring software.
Accounting and CPA firms
Our company helps CPA accounting firms monitor their network for newly discovered devices, and changes in data.
VPN Firewall and Router Vendors we can connect to AWS
We can help customers with their UTM and Sophos XG or other firewall models get connected to AWS cloud.
We can work with Cradlepoint IBR routers and other types of cellular routers to help you create SDN solution with direct access to the cloud over OpenTLS.
We can help your company have secondary level of remote IPSEC access directly to Pulse Secure Appliances installed in the form of AMI in AWS cloud.
We can help customers get integrated with Zscaler as primary method of communication for remote access VPN, with combination of some other vendor like Pulse Secure in AWS as secondary vendor.
We can help customers create VPN tunnels through transit gateways to CSRs hosted in AWS cloud from the remote branches and we can help run EIGRP over DMVPN tunnels or even OSPF.
We can work with GAIA R77 and up version appliances helping customers get connected to the cloud in either routed or policy based routing way.
We can help customers with Cisco ASA connectivity to AWS cloud, using active and standby type of fail over methods.
We can help with Edgerouter connectivity from behind the NAT devices.
We also work with customers who have FortiNET environment and seeking help to interconnect their on premise networks to AWS cloud either through built in native features of AWS using virtual private gateways or to Fortigate Appliances in AWS cloud.
Problems and AWS VPN Tunneling Solutions
With our AWS VPN tunneling solutions we can reduce the amount of complexity to minimum, helping you take control of your cloud based network, and assisting you with creating secure inter-connectivity.
Our company can help you dissect cost factors and provide you with recommended cost optimal VPN solution.
We can help you manage both of your environments, document your entire cloud based architecture as well as on premise architecture and also help you monitor it.
We can help you manage your VPN endpoints with certificate based authentication. We have dedicated solutions for CLM and PKI management, making certificate renewal easy to do.
Indeed, with new applications come and go, it can be tricky managing security groups. Our company can help with AWS Security management as well.
We have dedicated scanning and patching solution just for the vulnerabilities, and not only for the firewalls that terminating your VPN tunnels, but for other devices as well.
If you have DMVPN tunnels that needs integration with AWS we can help you integrate them helping your offices be directly connected to the cloud through DMVPN.
Other Integration and IT Services Similar to AWS VPN Tunneling Solutions that we offer
-
AlphaCICE & Alpha FusionView Service Details
Read moreMinimize false positive, duplicate alerts with AlphaCICE central intelligence correlation engine. AlphaCICE and unify all of your tools AIOPS events in a single pane of glass with Alpha FusionView. See how Alpha FusionSmart Enterprise Monitoring service that Alpha Technologies offer ties it all up together in context of multiple ITIL best practices phases.
-
AlphaCICE – Central Intelligence Correlation Engine
Read moreMinimize false positive, duplicate alerts with AlphaCICE central intelligence correlation engine. AlphaCICE is a custom solution and service offered by Alpha Technologies that is specifically designed for financial industries seeking to take control of their incident management process. Incident Managers can maximize their operational effectiveness through streamlined operationalized workflows, by relying on correlated supervised and unsupervised AIOPS classified intelligence fetched from your already existing monitoring tools. AlphaCICE is explicitly designed to reduce multiple events into a single actionable event that matters most, by empowering data owner operators with prescriptive & AI & ML driven recommendations
-

Alpha Digital Transformation of Applications & Tech Stack
Read moreAlpha Digital Transformation solutions for all size businesses seeking to secure their legacy application in order to minimize risk, while in parallel migrate the application and tech stack into modern API invokable and event driven ecosystem helping data owners get closer to their data.
-

Alpha AWS | AVD | Office 365 Virtualization Solutions
Read moreAWS Desktop and Network Virtualization solutions and services for small, medium & large size companies seeking to solve high latency connectivity related problems, while maximizing security.
-

Alpha FusionChain Innovative Solution for BlockChain Database and Monitoring
Read moreMigrate Your Legacy applications to Blockchain faster and safer without disruption of the existing workflow. With our tool kit we can help companies build, deploy maintain and manage Blockchain architecture helping you revolutionize your microservices and decentralized architecture. We can build Blockchain networks for multiple use cases ranging from NFTs, Crypto, MetaVerse and beyond.
