Identity as a Service Consulting Services

What is FusionAuth?
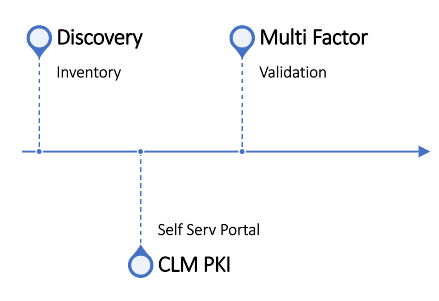
FusionAuth is a custom built Multi Factor Identity Validation as a Service solution created by DBA Binary Fusion company that encompasses best industry security practices and frameworks for companies wishing to validate their devices, users or applications prior to getting authenticated and authorized onto the network.
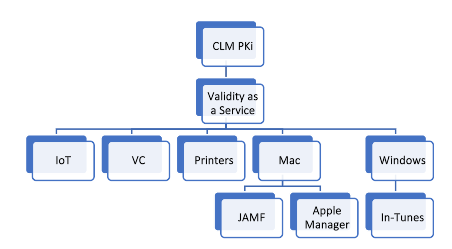
FusionAuth is basically a service that our company offers to customers who already may or may not have existing authentication and authorization solutions and looking for integration help. Our FusionAuth service encompasses FusionCLM solution offering that we specifically developed for customers seeking to take control of their certificate lifecycle management and PKI needs as it pertains to renewing certificates and maintaining your PK.
FusionCLM is basically a subset of FusionAuth service offering. Our FusionAuth service goes beyond just CLM and PKI
Go Beyond Certificates, with multi level identity.
Our company works with different types of vendors, helping customers reinforce their security with multi-factor level of validation for all of customers’ devices. Whether these devices are in cloud or on premise. c
So how do we help customers validate if device that hops on the network is a company device?
The answer is through the use of Cisco Identity Service Engine to tackle your on premise connectivity needs, and through integration of Cisco Identity Service Engine with MDM or multiple MDMs such as JAMF and Microsoft Endpoint Manager In-Tunes, in order to allow devices that are either mobile communicating with your company’s applications across multi cellular/wireless networks or on premise be able to connect securely, regardless if they are BYOD types of devices, IoT devices or any other enterprise appliances attempting to connect to your network such as printers, video conferencing systems or servers.
Beyond Certificate LifeCycle Management
Our company can go beyond just the certificate lifecycle management.
Relying on certificates to validate if the device is truly the company’s devices, is all great and good, however, it still does not protect from the security unfortunate situations where the certificate is copied from your company’s device to another on company’s device and such device end up hopping on your network causing all sorts of damage…
How do you combat that?
This is where our multi-factor monitoring and integration services come into play.
Imagine having multi level of validation
- Imagine having a way to rely not just on certificate lifecycle management, but on other methods of validation to fortify your security, where our company can help you integrate your network with Cisco Identity Services solution and MDM solution such as Azure Microsoft Endpoint MDM that can manage compliance access through In-Tunes or JAMF and provide solid intelligence to Cisco ISE in regards to devices’ compliance state.
Having a combination of both solutions side by side is like having brother and sister of network security and application security.
Our company can help customers with their network security fortification, where we can help your organization deploy Cisco ISE, roll out certificates across multiple devices, turn on 802.1x on wired and wireless devices, on the WLC controller level as well as Cisco Switches or any other 802.1x supported switches. We can help with deploying across the entire distributed environment, regardless if your company is national or multi-national.
- Think of Cisco ISE as a knight and shining armor who does not allow devices to hop on the network prior to devices validating themselves with ISE and MDM as truly trusted, based on the certificates that they contain or other types of posturing characteristics.
- Our company can also help customers move away from the traditional complex identity system and can help with integrating of Cisco ISE with Azure or other types of mult-factor IDPs. This way you can log in across your routers, switches, and firewalls with the very same AD username and password, attached to the Microsoft Authenticator application or any other type of application that will recognize the user as a legitimate user and prompt the user on their phone to accept authentication request any time someone logs into your network.
- Leveraging Cisco ISE for validating if the device that hops onto the network happens to be company’s device, is dependent on not just certificates, but also on other characteristics such as if the devices have a CrowdStrike agent installed or if it has in-tunes installed, or if there is specific registry string that makes the device unique.
- Multiple levels of validation are often required to combat situations where a certificate is stolen and copied into another non-legitimate device. Our company has developed integration expertise specifically for different types of devices, where we leverage MDM solutions such as Azure Endpoint Manager In-Tunes to identify if the device that hops on the network doesn’t just have a certificate, but also happens to be compliant with in-tunes. If it is then we allow devices on the network.
What exactly does our company offer for Multi Factor Identity Integration & Validation Services?
In addition, our company offers extenuation of our original CLM and PKI product offering for companies who would like to manage their Certificates Lifecycle process in combination with the PKI infrastructure and be able to have a centralized portal that allows customers to renew certificates in a single place vs jumping across different types of tools generating certificates and forgetting about them 3 years later only to result in outage.
Why validating what gets on your network matters.

Problem
Devices can get on company's network without any true form of validation:
The most typical solution to that problem is the deployment of certificates and managing these certificates throughout the entire certificate lifecycle management process. That means renewing certificates on devices such as video conferencing systems, phones, printers, security appliances, IoT devices, you name it.
Yet the reality is, not that many vendors out there actually support certificates. Many IoT devices simply have no way of inserting certificates or do not support EAP-TLS 802.1x authentication. Yet the need for security and validation of the devices is still there.
For every device there is a different Validation solution.
Depending on what type of device is trying to authenticate with the network, the authentication capabilities may vary. For example, some may support certificates, while others may support no such thing, but perhaps have some process or a service, or a registry key that is running in Windows OS for example.
IoT devices may have unique processes/services that can be tracked for validation.
Yet the problem is it’s hard to monitor devices that constantly come and go.
Imagine monitoring not just devices, but lambda functions and auto-scaling ec2 instances… that’s when the real fun begins.
Yet with every unique problem, there is a unique solution.
DBA Binary Fusion can help you tackle these Identity Validation problems with unique solutions.

Solution
So how do you validate different types of devices and applications if certificates can not exactly be deployed?
The answer is to use multiple layers of validation.
- For example if your environment consists of laptops that have operating systems such as Windows and MAC OS, then there are multiple validation tools that exist out there that makes the concept of recognizing that the the laptop is company’s laptop and not just some rogue device.
- Yet the reality is that many of the tools on the market require sophisticated level of understanding about all the eccentric functionalities.
- Many of the tools on the market makes concept of realizing what works or what doesn’t difficult to decipher.
- Managed windows devices maybe easier to handle with Enterprise application tools such as Microsoft Endpoint Manager (formerly known as in-tune), while MAC devices are easier to handle with tools like JAMF and Apple Business Manager.
- Yet what about other devices such as the ones that do not have certificate validation capabilities or enterprise MDM system to handle the requests, how can such types of devices be handled from validation standpoint?
Introducing Identity as a Service by DBA Binary Fusion
Multi Factor Identity Integration & Validation Services
- Imagine in addition to taking control of your PKI and CLM needs, from the centralize portal without you having to generate certs with 100 different processes for different types of devices and applications and appliances, be able to actually use additional levels of validation.
- Imagine being able to tell who is trusted and who is not with the help of intelligent Identity service engine?
- Imagine being able to validate not only your devices that are trying to get onto your network physically, but also being able to validate your VPN/DTLS users connecting through major VPN appliances such as Zscaler, Pulse Secure, Cisco AnyConnect, FortiVPN or others.
- Imagine being able to validate your users based on processes running on their pcs or file names or other attributes or characteristics.
- Imagine being able to not only validate your users based on different types of attributes, but also being able to see which devices hop on your network that were not previously identified.
- Imagine being able to see which new mac addresses showed up on your network regardless if they are wireless or wired or if they showed up through VPN.
- Imagine being able to see which devices are in compliance and categorized as trusted device and which ones are most likely rogue.
- Imagine being able to white list new mac-addresses or devices that are questionable and generate a ticket in Service Now.
- Imagine being able to pass this information into ticketing systems, keeping security folks happy and leaving record trail.
- Imagine being able to visualize graphically inventory of your trusted and not trusted devices geographically or using any other levels of grouping.
- Imagine being able to view flow logs, ranging from Amazon CloudTrail, netflow and other data sources.
- Imagine being able to have it all stitched together based on your company’s needs with the flexible logic that displays and visualizes everything for your Operation, Executive, and IT teams in a unified Tony Stark View.
- Imagine being able to get notified if the device that hopped on the network meets certain characteristics, where such characteristics can be gathered from multiple security appliances and intelligence systems into your existing SIEM or specifically crafted unified tool that combines both Certificate Life Cycle Management of your PKI, mac address white listing functionality helping you determine what new device got on the network that wasn’t recognized before and meets certain non-trustful characteristics.
In addition to offering multi factor level of validation across either certificates or other validation characteristics also being able to visualize your entire environment in tools like New Relic,DataDog, LogicMonitor, SumoLogic, AppDynamics, Zenoss or Splunk, Solar Winds.
- Imagine being able to visualize your configuration changes on switches, routers or firewalls, as well as changes within your infrastructure environment ranging from actual physical infrastructure as well as cloud, whether it’s Kubernetes clusters or Serverless Microservices.
- Imagine being able to visualize business transactions as it pertains to generic health score of your entire application or business service, or being able to visualize unique business processes not just from metric standpoint, but from logs.
- Imagine being able to visualize distributed tracing patterns as users navigate through different types of business transactions and how overall health of your application depends on the infrastructure components, application components and other dependencies.
- Imagine being able to visualize even complex recurring events that need to be factored into alerting, but require intelligent logic adjustment.
- Imagine being able to suppress alerts and tackle seasonal type of data, in order to minimize risk of not being alerted when you needed vs when alert is not really needed.
- Imagine being able to have predictive and forecasting monitoring that can combine previous cyclical data in combination with other factors that are relevant for your environment and be able to get alerted on that.
- Imaging having different types of dashboards for compliance, operational level and many other levels, in combination with repots being sent to you or other team members helping your team minimize risk and look like a super hero.
Well with so many imaginative points... described above, you do not have to imagine anymore.
Simply reach out to our DBA Binary Fusion company tell us your use case and we’ll hit the ground running supplementing your existing IT Staff with super charged monitoring and cyber security expertise, that can help your organization reduce risk and best of all tackle complicated tasks that otherwise would not be possible to tackle without a strong IT Security and Network/Application monitoring expertise.
When contacting us, simply let us know the use case you are working on, what you are trying to integrate, what you need monitored, how you are trying to integrate, what tools you already invested and need help with. Or simply describe the challenge you are facing. Our company is very agile and flexible in the way we conduct business. If interested in our services feel free to reach out to us, so we can share with you some of our service offering demonstrations and see if we can do POC or POV for you.
We work with financial organizations as our core expertise, but also service other types of industries ranging from real-estate, manufacturing, professional LLCs, accounting firms, health/medical dental, entertainment industries and other types of industries.
In Summary
- Reach out to us, let us know your use case, we can get together analyze what you have, and provide your recommendation on how to move forward with what tool, what to monitor, how to monitor it and can also provide you presentation for some of the services that we did for our other customers in the field of Machine Learning, Certificate LifeCycle Management, Network Monitoring and beyond.
- If interested send an email to [email protected] and simply let us know your name, company name, phone number, and what you are looking for, or alternatively contact us by the phone number shown on the top right corner of this website.
- Thank You for taking your time to read about our Logic Monitoring Services and Solution Integration services.
Industries We Service and help customers integrate Multi Factor Solutions
Travel and Aviation
Consulting
We help companies monitor Airport Networks and ATM devices, as well as wireless access points.
Financial Services
Consulting
Our company helps Loan Processing firms, Banks, and other financial institutions monitor combination of both on premise and in cloud resources.
Education
With Entuity we can monitor Campus networks for real time changes on infrastructure such as firewalls, routers, switches, SDN controllers.
Law Firms
We also work close with Law Firms and other types of legal organizations seeking to monitor their cloud and on premise resources.
Manufacturing
Our company can help customers add foam spray pumps, or any other types of manufacturing devices, or IoT devices into Entuity monitoring software.
Accounting and CPA firms
Our company helps CPA accounting firms monitor their network for newly discovered devices, and changes in data.
Devices we can help validate
We can validate your entire fleet of printers prior to them getting on the network with 802.1x certificates. We can roll out the certs on all the supported printers, then configure Cisco ISE policies to validate printers prior to printers getting on the network.
We can ensure that your Web Ex or Zoom or Cisco based devices are on 802.1x, we can also help you manage them in the cloud as well as validate them prior to any of these devices getting on your network.
We can validate your Cisco IP Phones as well, by leveraging your existing CUCMs to roll out the LSC and MIC certs and create self provision policies to allow certificate deployment globally.
We can create JAMF or Microsoft Endpoint Manager formerly known as Intunes to validate your existing devices as part of the compliance module, prior to getting your windows and mac devices on the network. We can roll out both machine and user certs, for wired and wireless use cases.
We can validate Servers IoT and other types of infrastructure devices prior to them getting on the network, regardless if they are ESX virtual or if they happen to be running as on EC2 instance.
Problems and Multi Factor Validation Solutions
With multi factor identify validation services, DBA Binary Fusion can help customers integrate Identity validation solutions, that can identify if device belongs to company’s organization.
Our company can help onboard many different types of devices on premise or in cloud with certificates and integrate them with 802.1x Cisco ISE, helping customers take control of their network.
Once all devices are on 802.1x we can and validated as company’s devices, it will be a lot easier to see which new device is not on 802.1x. Our Monitoring and Identity Integrations solutions can help.
We can help customers visualize what validated devices are on 802.1x geographically, helping customers easier troubleshoot issues.
Certificates importation is not the answer for everything, sometimes different validation tools are required for different jobs. With the help of DBA Binary Fusion Validation as a Service solutions, we can help customers validate IoT devices.
With the introduction of additional levels of validation, your number of major incidents will be reduced.
Other Integration and IT Services Similar to Multi Factor Validation services that we offer
-
AlphaCICE & Alpha FusionView Service Details
Read moreMinimize false positive, duplicate alerts with AlphaCICE central intelligence correlation engine. AlphaCICE and unify all of your tools AIOPS events in a single pane of glass with Alpha FusionView. See how Alpha FusionSmart Enterprise Monitoring service that Alpha Technologies offer ties it all up together in context of multiple ITIL best practices phases.
-
AlphaCICE – Central Intelligence Correlation Engine
Read moreMinimize false positive, duplicate alerts with AlphaCICE central intelligence correlation engine. AlphaCICE is a custom solution and service offered by Alpha Technologies that is specifically designed for financial industries seeking to take control of their incident management process. Incident Managers can maximize their operational effectiveness through streamlined operationalized workflows, by relying on correlated supervised and unsupervised AIOPS classified intelligence fetched from your already existing monitoring tools. AlphaCICE is explicitly designed to reduce multiple events into a single actionable event that matters most, by empowering data owner operators with prescriptive & AI & ML driven recommendations
-

Alpha Digital Transformation of Applications & Tech Stack
Read moreAlpha Digital Transformation solutions for all size businesses seeking to secure their legacy application in order to minimize risk, while in parallel migrate the application and tech stack into modern API invokable and event driven ecosystem helping data owners get closer to their data.
-

Alpha AWS | AVD | Office 365 Virtualization Solutions
Read moreAWS Desktop and Network Virtualization solutions and services for small, medium & large size companies seeking to solve high latency connectivity related problems, while maximizing security.
-

Alpha FusionChain Innovative Solution for BlockChain Database and Monitoring
Read moreMigrate Your Legacy applications to Blockchain faster and safer without disruption of the existing workflow. With our tool kit we can help companies build, deploy maintain and manage Blockchain architecture helping you revolutionize your microservices and decentralized architecture. We can build Blockchain networks for multiple use cases ranging from NFTs, Crypto, MetaVerse and beyond.
